In today’s hyperconnected world, where businesses rely heavily on digital infrastructure and data, cyber threats have become more than just a technical concern—they’re a financial and reputational risk. From ransomware attacks to data breaches, cyber incidents can disrupt operations, erode customer trust, and cost companies millions. That’s where cyber insurance comes in. Much like traditional insurance protects against physical damages or liabilities, cyber insurance shields your business from the costly aftermath of digital attacks. In this article, we’ll break down what cyber insurance is and explore how it helps protect against the growing wave of cyber threats in the modern digital landscape.
What is Cyber Insurance?
Cyber insurance, also known as cyber liability insurance, is a specialized form of coverage designed to protect businesses from the financial consequences of cyber incidents. These incidents can include data breaches, ransomware attacks, phishing scams, and other malicious digital activities that compromise sensitive information or disrupt operations. Just as property insurance covers damage to physical assets, cyber insurance helps cover the costs associated with responding to a cyberattack—such as legal fees, data recovery, customer notifications, and system repairs. By transferring some of the financial risk to an insurer, cyber insurance allows organizations to better manage the fallout of digital threats and maintain stability in an increasingly vulnerable online environment.
Why is Cyber Insurance Important?
Cyber insurance is essential because no matter how advanced a company’s security measures are, the risk of a cyberattack is never zero. As businesses grow more reliant on digital tools, cloud services, and online data storage, the potential impact of a breach or ransomware attack becomes increasingly severe. A single incident can lead to significant financial losses, legal complications, reputational damage, and business disruption. Cyber insurance acts as a financial safety net, helping organizations recover quickly by covering costs such as legal support, regulatory fines, system restoration, and public relations efforts. It not only minimizes the financial burden but also supports business continuity and customer trust in the aftermath of a cyber-event.
 How Does Cyber Insurance Protect Against Digital Threats?
How Does Cyber Insurance Protect Against Digital Threats?
In today’s digital world, even the most secure networks can be breached. Cyber insurance doesn’t stop attacks from happening, but it plays a vital role in helping businesses recover from the financial, legal, and operational consequences. Here’s a closer look at how it works:
1. Covers Financial Losses from Cyber Incidents
When a cyberattack strikes, the costs can quickly spiral—ransom payments, halted business operations, lost sales, and customer refunds. Cyber insurance helps absorb these unexpected financial hits. For example, if a ransomware attack locks your systems and halts production for several days, the policy may cover the revenue lost during that downtime.
2. Funds Data Breach Response and Notification
Most jurisdictions require businesses to notify customers when their personal data is compromised. This process includes mailing letters, setting up hotlines, and offering credit monitoring. Cyber insurance covers these notification expenses and the logistics that follow, ensuring compliance with privacy laws while helping protect your brand’s trust.
3. Supports Legal and Regulatory Compliance
Cyber incidents often trigger regulatory investigations, especially if sensitive data like medical records or financial details are involved. Cyber insurance can pay for attorneys, settlement costs, and penalties resulting from violations of data protection laws (such as GDPR or HIPAA). This helps you navigate complex legal landscapes without overwhelming your internal resources.
4. Pays for System Repairs and Data Recovery
Once the breach is contained, businesses must restore compromised IT systems and recover lost or corrupted data. This can involve reconfiguring networks, restoring backups, and securing endpoints. Cyber insurance helps pay for these technical recovery efforts, speeding up the return to normal operations and minimizing additional disruption.
5. Provides Crisis Management and PR Support
Reputation damage can linger long after a cyberattack. If customer trust erodes, so can future sales and partnerships. Cyber insurance often includes access to public relations firms or crisis communication experts who can help craft messages, handle media inquiries, and protect your brand image during and after a cyber-event.
6. Assists with Ransomware and Extortion Incidents
Some of the most devastating attacks today involve ransomware—where criminals encrypt your data and demand payment to restore access. While some insurers are now limiting this coverage, many policies still help with negotiating ransom demands, managing payment logistics, and coordinating with law enforcement, especially when paying the ransom is the only viable option.
7. Grants Access to Cybersecurity Experts
During a cyber-crisis, having the right experts on your side can make all the difference. Cyber insurance providers often include or recommend cybersecurity vendors—such as digital forensics teams, malware analysts, and IT specialists—who can quickly assess what happened, stop the attack, and provide insights to prevent future incidents.
8. Protects Against Third-Party Liability Claims
If your data breach impacts customers, vendors, or business partners, they might sue your organization for negligence. Cyber insurance provides third-party coverage to handle these claims, covering attorney fees, court costs, settlements, or judgments—so one breach doesn’t snowball into multiple costly lawsuits.
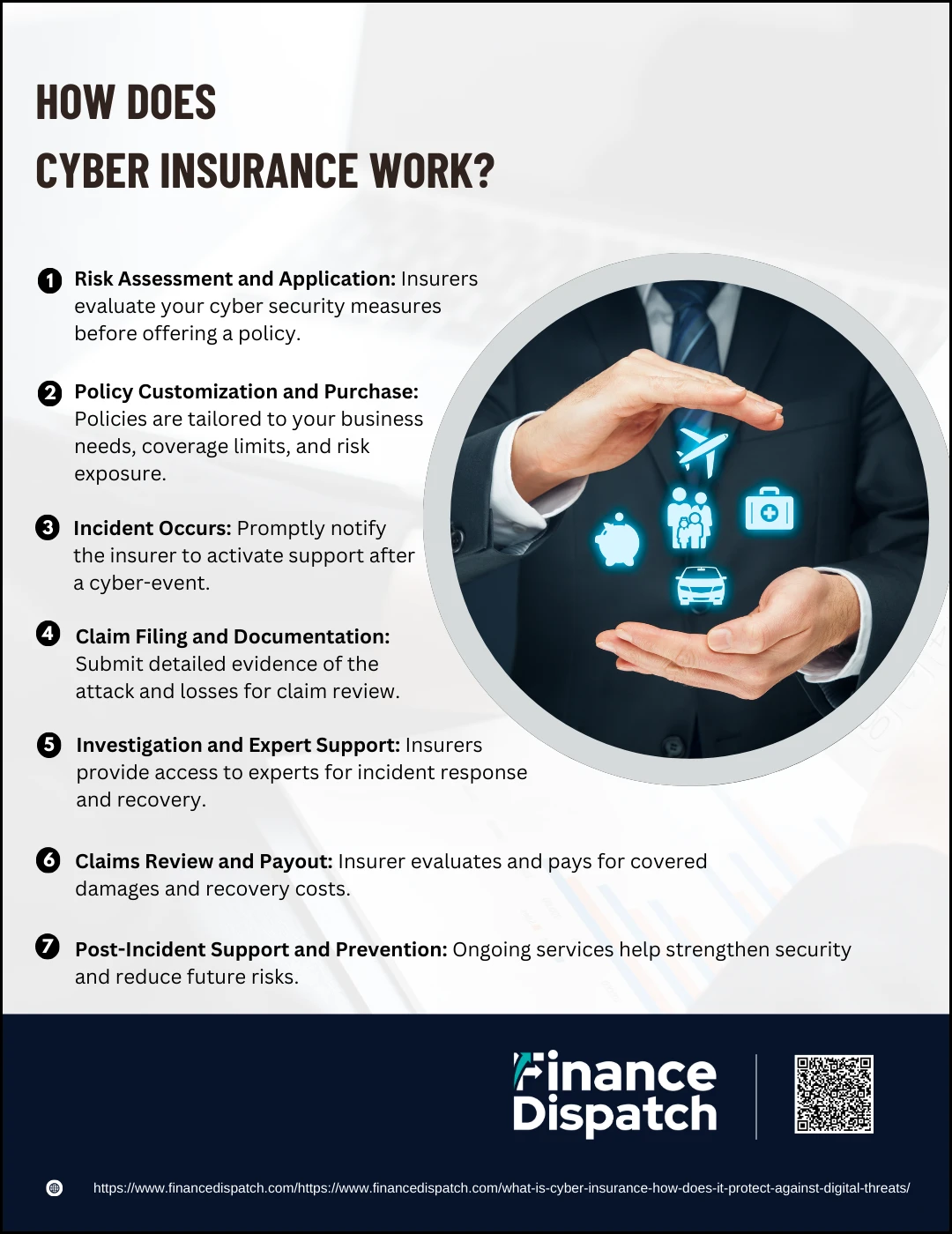 How Does Cyber Insurance Work?
How Does Cyber Insurance Work?
Cyber insurance provides a safety net for businesses operating in today’s digital-first world. But it’s not as simple as just signing up and being covered. From risk evaluations to post-incident recovery, cyber insurance involves a structured process to ensure the right coverage is in place—and that claims are handled efficiently when cyber threats strike. Here’s a detailed breakdown of how cyber insurance actually works:
1. Risk Assessment and Application
Before issuing a policy, insurers assess the security posture of your business. This can involve completing questionnaires, submitting to cybersecurity audits, or providing documentation about current protection measures like firewalls, data encryption, multi-factor authentication (MFA), and employee awareness training. Businesses with stronger security controls are often eligible for broader coverage and lower premiums, while those with gaps may need to improve their defenses before qualifying.
2. Policy Customization and Purchase
No two cyber insurance policies are the same. After assessing your risk level, the insurer works with you to tailor a policy that fits your industry, data exposure, and risk tolerance. You’ll choose coverage limits (the maximum the insurer will pay), deductibles (what you pay before insurance kicks in), and decide between first-party coverage (your internal losses) and third-party coverage (liabilities to others). Once terms are finalized, the policy becomes active upon payment.
3. Incident Occurs
When a cyber event happens—whether it’s a phishing scam, ransomware attack, data breach, or denial-of-service (DoS) incident—your response time is crucial. Most cyber insurance policies require you to notify your provider within a specific timeframe (often within 24–72 hours). The sooner the insurer is alerted, the sooner support and resources can be deployed to contain the damage.
4. Claim Filing and Documentation
You begin the formal claims process by submitting details of the incident. This typically includes timelines of the attack, forensic reports, financial records showing loss or damage, logs of compromised systems, and any regulatory or legal notices. Thorough and accurate documentation speeds up the review and improves your chances of a full reimbursement.
5. Investigation and Expert Support
One of the biggest advantages of cyber insurance is the access it provides to cybersecurity professionals. Most insurers partner with incident response teams, forensic investigators, legal advisors, and crisis communication experts who assist in containing the threat, recovering systems, complying with laws, and restoring public trust. These services are often coordinated and funded by the insurer directly.
6. Claims Review and Payout
The insurer reviews your submitted claim to ensure it aligns with the coverage specified in your policy. They assess the financial losses, verify costs, and evaluate liability. Once approved, the insurer issues payment to cover eligible expenses, which may include ransom payments (if legal), data recovery, system repair, business interruption costs, regulatory fines, and legal defense.
7. Post-Incident Support and Prevention
After the crisis is over, many cyber insurance providers offer post-breach services. These may include vulnerability assessments, cybersecurity training for staff, software recommendations, and guidance to close the gaps that led to the attack. This proactive support helps your business reduce the chance of future incidents and may improve your insurability or lower premiums during renewal.
What Does Cyber Insurance Cover?
Cyber insurance is designed to help businesses recover from the financial and operational impact of cyber incidents. While coverage may vary depending on the provider and policy terms, most plans offer protection for both direct damages and liabilities resulting from cyberattacks, data breaches, and other security failures. This coverage can make the difference between a swift recovery and long-term disruption. Here are the key areas typically covered by cyber insurance:
- Data Breach Response
Covers the cost of identifying the breach, notifying affected individuals, offering credit monitoring, and handling public relations to protect your reputation. - Business Interruption
Compensates for lost income and operating expenses when your systems go offline due to a cyberattack or security failure. - Ransomware and Extortion Payments
Pays for ransom demands, negotiation costs, and related expenses when attackers lock your data or threaten to release sensitive information. - Legal and Regulatory Costs
Covers attorney fees, court costs, and regulatory fines resulting from violations of data protection laws or lawsuits by affected parties. - System and Data Restoration
Helps recover or rebuild damaged IT infrastructure and restore lost or corrupted data after a cyber-incident. - Forensic Investigation
Pays for experts to identify how the attack occurred, what was affected, and how to prevent future incidents. - Crisis Management and Public Relations
Provides access to professionals who manage media, customer communication, and brand reputation in the wake of an attack. - Third-Party Liability
Covers claims from clients, partners, or vendors affected by a cyber-incident that originated from your business. - Fraud and Social Engineering
Some policies cover financial losses due to scams like phishing emails or fraudulent fund transfers caused by manipulated employees.
What is Not Covered by Cyber Insurance?
While cyber insurance provides vital protection against a wide range of digital threats, it doesn’t cover everything. Like all insurance policies, cyber coverage has exclusions and limitations that businesses must understand to avoid surprises during a claim. These exclusions often relate to preventable incidents, internal issues, or specific types of damage that fall outside the policy’s scope. Knowing what isn’t covered helps ensure you have a well-rounded cybersecurity strategy and realistic expectations. Below are common exclusions typically not covered by cyber insurance:
- Pre-existing Incidents
Any cyber event that occurred before the policy start date is generally excluded from coverage. - Known but Unaddressed Vulnerabilities
If your systems were already exposed due to a known flaw and you failed to fix it, related breaches may not be covered. - Insider Threats and Employee Misconduct
Damage caused intentionally by employees or through gross negligence may fall outside of coverage. - Failure to Maintain Security Standards
Claims may be denied if your business did not follow basic cybersecurity practices outlined in the policy requirements. - Criminal and Regulatory Penalties
Some policies exclude criminal fines, penalties from intentional law violations, or punitive damages. - Infrastructure Failures Not Caused by Cyber Events
Power outages, utility failures, or hardware malfunctions unrelated to cyberattacks are typically not covered. - Reputational Damage and Long-Term Revenue Loss
While some policies help with PR costs, losses from long-term brand damage or valuation decline are rarely included. - Upgrades and Security Improvements
Costs to improve, replace, or upgrade your IT systems after an attack—such as new software or hardware—are usually not reimbursed. - Acts of War or State-Sponsored Attacks
Some insurers exclude cyberattacks believed to be linked to nation-states, categorizing them as acts of war.
First-Party vs. Third-Party Coverage
Cyber insurance policies are typically divided into two main types of coverage: first-party and third-party. Understanding the difference between the two is essential when choosing the right protection for your business. First-party coverage protects your organization from direct losses resulting from a cyber- incident such as data restoration, lost revenue, or ransom-ware payments. On the other hand, third-party coverage addresses claims made against your business by external parties affected by the breach, including customers, clients, or regulators. Here’s a comparison of what each type of coverage typically includes:
| Coverage Area | First-Party Coverage | Third-Party Coverage |
| Data Breach Response | Covers internal costs for investigating and managing a breach | Covers liability if clients’ or partners’ data is exposed |
| Business Interruption | Compensates for lost income during system downtime | Not typically included |
| Ransom-ware and Extortion | Pays for ransom demands and related expenses | Not typically included |
| System and Data Restoration | Covers restoring damaged systems and lost data | Not typically included |
| Forensic Investigation | Pays for identifying the cause and scope of a cyber-attack | Sometimes included for legal defense preparation |
| Legal Defense Costs | May cover your internal legal team’s response | Covers legal costs from lawsuits or regulatory claims |
| Regulatory Fines and Penalties | Occasionally included, depending on policy | Commonly included for claims by regulators |
| Reputation Management | Covers PR and crisis communication efforts to protect brand image | May include compensation for reputational harm to third parties |
| Third-Party Claims | Not included | Covers lawsuits, settlements, and damages from affected parties |
Choosing the Right Cyber Insurance Policy
Selecting the right cyber insurance policy involves more than comparing prices—it requires a clear understanding of your organization’s specific risks, data sensitivity, and regulatory responsibilities. Not all policies are created equal, and coverage can vary significantly between providers. Start by assessing your cyber risk profile: what types of data you store, how critical your digital systems are, and whether you’ve experienced breaches in the past. Look for policies that offer both first-party and third-party coverage, and ensure the limits and exclusions align with your needs. It’s also important to consider the insurer’s support services, such as access to incident response teams or legal counsel, which can be invaluable during a crisis. Reviewing the fine print, consulting with a cyber-insurance broker, and conducting a security audit before applying can help you secure a policy that offers effective, tailored protection for your business.
Requirements to Qualify for Cyber Insurance
Before an insurer agrees to provide cyber insurance coverage, your business must meet certain cybersecurity standards and demonstrate responsible data protection practices. These requirements help reduce the risk of claims and ensure that your organization is prepared to prevent, detect, and respond to cyber threats. While requirements may vary by insurer and industry, most policies share a common set of baseline expectations. Fulfilling these not only improves your chances of getting approved but may also lead to better coverage terms and lower premiums. Here are some common requirements to qualify for cyber insurance:
- Multi-Factor Authentication (MFA)
Required for securing access to critical systems and accounts, especially remote access and administrator privileges. - Firewall and Antivirus Protection
Demonstrating the use of up-to-date firewalls, antivirus software, and endpoint protection solutions is essential. - Regular Software Updates and Patch Management
Systems must be kept current with the latest security patches to reduce exposure to known vulnerabilities. - Data Encryption
Sensitive data should be encrypted both at rest and in transit to minimize risks of unauthorized access. - Access Control Policies
Implementing strict user access controls and the principle of least privilege helps limit potential damage from breaches. - Employee Cybersecurity Training
Staff should undergo regular training to recognize phishing, social engineering, and other common threats. - Incident Response Plan
A documented and tested response plan ensures your business can act quickly and efficiently during a cyber-incident. - Data Backup and Recovery Protocols
Regular backups and a clear recovery process are critical for minimizing downtime after an attack. - Vendor Risk Management
Insurers may review how your business manages cybersecurity risks related to third-party vendors or partners. - Security Assessments and Audits
Some insurers require independent security assessments or penetration testing to evaluate your risk posture.
Cost of Cyber Insurance
The cost of cyber insurance can vary widely depending on several factors unique to your business. While small businesses might pay a few hundred dollars per month, larger organizations or those in high-risk industries may face significantly higher premiums. Insurers calculate these costs based on your company’s risk profile, coverage limits, and the strength of your existing cybersecurity measures. Understanding what influences the price of cyber insurance can help you manage costs and find a policy that offers the best value for your needs. Here are the key factors that affect the cost of cyber insurance:
- Company Size and Revenue
Larger businesses with higher annual revenue typically pay more due to the increased potential exposure and larger scale of operations. - Industry Type
Companies in high-risk sectors like healthcare, finance, and retail often face higher premiums due to the sensitive nature of the data they handle. - Volume and Sensitivity of Data
Businesses storing large amounts of personal, financial, or health information are considered higher risk and may pay more for coverage. - Cybersecurity Measures in Place
Strong cybersecurity practices—such as MFA, encryption, regular backups, and staff training—can help lower premiums. - Claims History
A history of previous cyber insurance claims may increase your premiums or limit your coverage options. - Coverage Limits and Deductibles
Higher coverage limits provide more protection but come with increased costs. Similarly, choosing a lower deductible may raise your monthly premium. - Policy Inclusions and Exclusions
The more comprehensive the coverage (e.g., inclusion of ransomware payments, business interruption, or third-party liability), the higher the premium is likely to be. - Geographic Location
Businesses operating in regions with stricter data protection regulations or higher cybercrime rates may pay more for insurance.
Who Needs Cyber Insurance?
Any business that uses digital systems, stores sensitive data, or operates online can benefit from cyber insurance. This includes organizations of all sizes and industries—from small retailers and healthcare providers to financial institutions and tech companies. If your business collects personal information, processes payments, relies on cloud-based services, or uses email for communication, you’re exposed to cyber risks like data breaches, ransomware, and phishing attacks. Even companies with strong cybersecurity defenses aren’t immune to threats. Cyber insurance provides a crucial safety net, helping businesses recover quickly and minimize financial losses when digital disruptions occur. In today’s connected world, cyber insurance is no longer optional—it’s a smart investment in your company’s resilience.
Examples of Covered Cyber Threats
Cyber insurance policies are designed to protect businesses against a wide range of digital threats that can disrupt operations, compromise sensitive information, and lead to significant financial losses. While the exact threats covered may vary depending on the insurer and policy type, most comprehensive plans include protection against common and high-impact cyber incidents. Here are some typical examples of cyber threats that are often covered by cyber insurance:
- Ransomware Attacks
Malicious software encrypts your data and demands payment for its release. Coverage often includes ransom payments, recovery costs, and business interruption losses. - Phishing Scams
Deceptive emails or messages trick employees into revealing login credentials or transferring funds. Insurance may cover the resulting financial loss and investigation costs. - Data Breaches
Unauthorized access to customer or employee data, including personally identifiable information (PII), often triggers coverage for notification, credit monitoring, and legal expenses. - Business Email Compromise (BEC)
Attackers impersonate executives or vendors to manipulate employees into transferring money or sensitive information. Cyber insurance can help recover the stolen funds and cover related losses. - Distributed Denial-of-Service (DDoS) Attacks
Flooding a company’s servers with traffic to cause downtime. Coverage may include lost income, mitigation services, and system repair. - Malware Infections
Software designed to harm or exploit computer systems. Insurance may pay for cleanup, system restoration, and security upgrades. - Cyber Extortion
Threats to release sensitive information or disrupt operations unless a demand is met. Policies often cover the cost of negotiations and potential payments. - Insider Threats (Malicious or Accidental)
Damage caused by employees misusing access or making critical errors. Some policies may cover these incidents if not excluded. - Social Engineering Fraud
Manipulation tactics used to deceive employees into taking unauthorized actions, such as wiring funds or sharing credentials. Coverage varies but may be included as an add-on.
Future of Cyber Insurance
As cyber threats continue to evolve in complexity and scale, the future of cyber insurance is expected to become more dynamic, data-driven, and tightly integrated with cyber security practices. Insurers are increasingly leveraging artificial intelligence, threat intelligence, and real-time monitoring to assess risk more accurately and tailor coverage accordingly. Policies may become more industry-specific, offering customized protections based on unique digital vulnerabilities. Additionally, as regulatory requirements around data privacy grow stricter, cyber insurance will likely play a bigger role in helping businesses remain compliant. We can also expect insurers to place greater emphasis on proactive risk management—rewarding companies that implement strong cyber security measures with lower premiums and broader coverage. Ultimately, the future of cyber insurance lies in a more collaborative approach between insurers and insured businesses, focused not just on recovery, but on prevention and resilience.
Conclusion
Cyber insurance has become a critical safeguard in today’s digital landscape, offering businesses the financial protection and expert support needed to recover from cyber incidents. While it doesn’t prevent attacks, it plays a vital role in minimizing damage, reducing downtime, and maintaining trust with customers and partners. From covering the costs of data breaches and ransom ware to helping manage legal and regulatory fallout, cyber insurance is a powerful tool in any organization’s risk management strategy. As threats continue to evolve, so too must your approach to security—and that includes having the right cyber insurance policy in place. Investing in cyber insurance isn’t just about managing risk; it’s about ensuring business continuity and long-term resilience.



